思科认证640-802模拟试卷29
试卷名称:思科认证640-802模拟试卷28

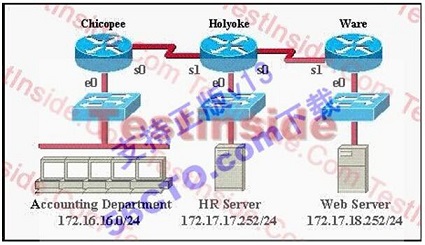
A.permit ip any any deny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80
B.permit ip any any deny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80
C.deny tcp 172.17.17.252 0.0.0.0 172.16.16.0 0.0.0.255 eq 80 permit ip any any
D.deny tcp 172.16.16.0 0.0.0.255 172.17.17.252 0.0.0.0 eq 80 permit ip any any
您可能感兴趣的题目
相关试卷
思科认证640-802模拟试卷29
思科认证640-802模拟试卷28
思科认证640-802模拟试卷27
思科认证640-802模拟试卷26
思科认证640-802模拟试卷25
思科认证640-802模拟试卷24
思科认证640-802模拟试卷23
思科认证640-802模拟试卷22
思科认证640-802模拟试卷21
思科认证640-802模拟试卷20
思科认证640-802模拟试卷19
思科认证640-802模拟试卷18
思科认证640-802模拟试卷17
思科认证640-802模拟试卷16
思科认证640-802模拟试卷15
思科认证640-802模拟试卷14
思科认证640-802模拟试卷13
用Cisco控制器进行简单网络配置和监控、将独立AP转换为LWAPP练习试卷1
无线网络概念、标准机构练习试卷1
无线流量和AP发现、其他无线技术练习试卷1